Open Source Platform based applications nowadays are extensively being considered by many business houses, for certain list of benefits & advantages. Some benefits extracted from Open Source Platforms are - source code being available in public domain, logically certain functional code would be reviewed & maintained by more than certain group of developers thus issues & loopholes would be minimum, Open Source Applications have flexible & adaptive approach towards application development. And to add a major plus point to the list of advantages is, Open Source Applications are available with no cost (free) of development.
Differentiate between Open Source Applications Vs Closed Source Application
In comparison with Closed Source Platform, Open Source Platform often scores highly with factors such as flexibility & cost effectiveness.
Having said that, Application Security remains one of the major concern while dealing with Open Source Platform. Certain degree of flaws may be present in Open Source Components, because while development future versions of programming language may not be considered, it would not have been adequate testing of the application may not have been done etc.
Now let us gain an insight over brief Application Security Constraints & measures to address these application security concerns.
Open Source Platform Adoption Statistics
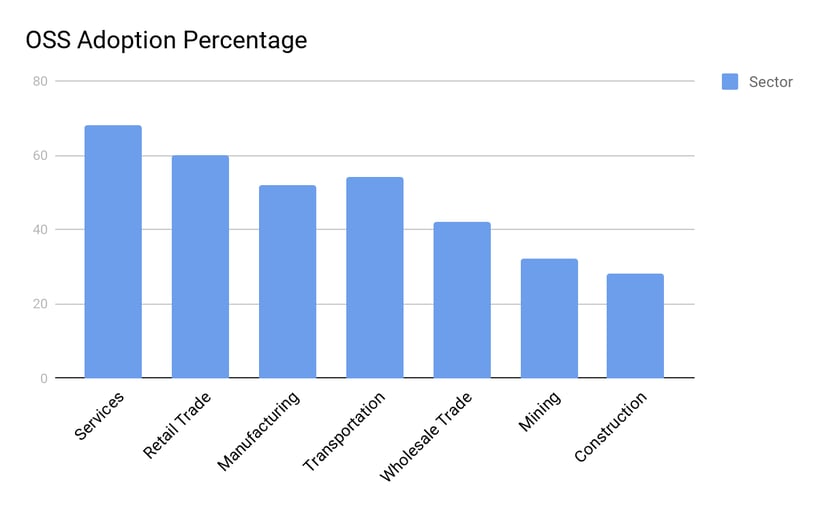
Reference: https://goo.gl/gpu71Y
Having said that, Application Security remains one of the major concern while dealing with Open Source Platform. Certain degree of flaws may be present in Open Source Components, because while development future versions of programming language may not be considered, it would not have been adequate testing of the application may not have been done etc.
Now let us gain an insight over brief Application Security Constraints & measures to address these application security concerns.
What is Application Security?
Application Security is a practise or set of activities involved in various stages of Software Development Life Cycle (SDLC) such as - Design, Development, Testing, Integration, Maintenance to enhance security of application, address possible/potential security vulnerabilities, continuous monitoring to prevent unforeseen security concerns.
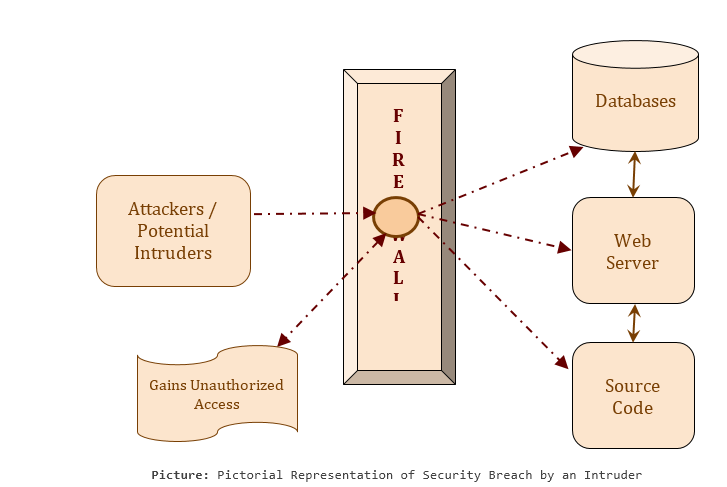
Application Security Statistics?
Following graph speaks about statistics specific to security threats being observed in recent times.
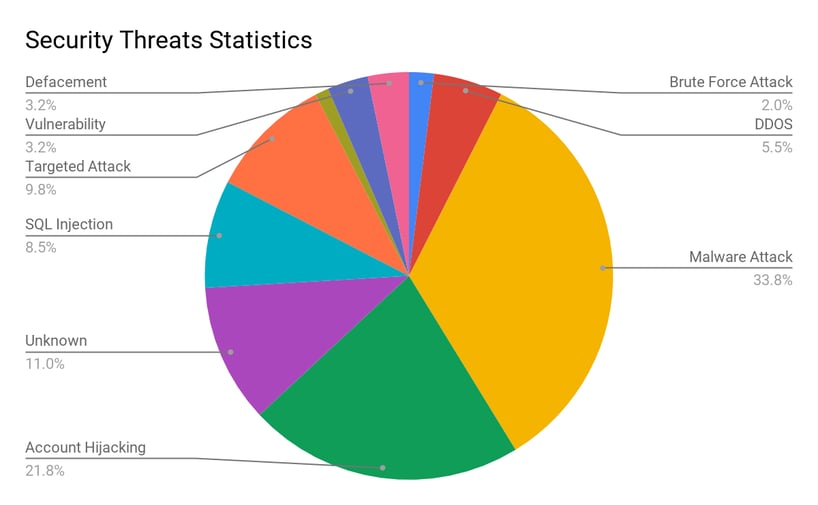
Reference: https://goo.gl/zgDFaF
Common Application Security Concerns
Generally attackers use following techniques / methods to breach securities in an application.
a. Session / Cookie Hijacking / IP Spoofing
Session / Cookie Hijacking / IP Spoofing is a technique used to tamper application's session / cookie keys to gain unauthorized remote access to the application.
General example of IP Spoofing is “Denial of Services” attack. In this type of attack intruder uses source routed IP packets, and overloads network.
b. SQL Injection / Cross Site Scripting (XSS)
SQL Injection / Cross Site Scripting refers to insertion / injection of client side scripts / code to execute malicious scripts.
Example : SQL injection malicious script is permanently stored in a database of application server, and executes the script whenever it's reference is called.
c. Brute Force Attacks
Brute force attack is a method used by attackers to decode encrypted data (Data Encryption Standard keys (DES) or Passwords) through a series of continuous attacks (brute force) until security breach is established. This kind of attack may span from hours to days.
Example of Brute Force Technique is to perform continuous and timely operations to crack password / sensitive data encryption process.
d. Software Code Tampering
Software tampering is a method of unauthorized alterations in a program code in a software application.
Example of Software Code Tampering involves a reverse engineering technique to break software code bit by bit and test its impact. This process is followed until security breach occurs.
e. Cross-Site Request Forgery (CSRF)
In Cross-Site Request Forgery (CSRF) kind of attack, attackers infuses a code so that end authenticated user would execute an unwanted actions on a web application.
Example of CSRF attack is “Phishing”. A technique which involves an attempt to retrieve personal & sensitive information from end users such as passwords, credit card numbers etc.
f. Security Misconfiguration
In Security Misconfiguration, an attacker gains an unauthorized access to the system to access default accounts, unprotected files / folders, old versions of plugins with security loopholes, unused pages / plugins / extensions.
Generic example of “Security Misconfiguration” specific attack occurs, because security settings in development environment & libraries of many applications are susceptible to threats and many a times the same environment is considered while making pushing application on production.
Application Security Measures for Open Source Platform
a. Application Security Testing & Manual Testing
With advent of automated testing constraints in development processes many dynamic analysis & static analysis tools are used to detect common code defects & security vulnerabilities.
But still, certain classes of security vulnerabilities may get un-noticed by automation tools. So in such a scenarios manual testing of application is required to keep a track of potential threats as far as security is concerned.
b. Static & Dynamic Analysis
Static analysis is done with the processes such as inspection of code in programs for all possible potential threats to prevent malicious code entry into application. Usually this process is taken care while development is in progress or during maintenance phase.
Dynamic analysis approach is a run-time process, it is done while a program / application is being executed.
c. Integrate Open Source Testing in DevOps Operations
Along with a process of automation of quality audits, a methodology to integrate automated security specific tests can also be an efficient & effective process.
In automation of testing process using tools like Selenium/WebDriver, testing of security features such as authentication etc.
d. Security Updates & Patch Upgrades
Schedule a timely activity of maintaining and applying security updates & patch upgrades within an application, in order to keep security concerns at the bay.
e. Monitor - New threats
Keep a frequent check for security threats & security specific updates being released by community on periodic basis.
f. User Management & User Access Levels
Keep a track on list of frequently visiting users & their activities. If possible remove obsolete users & downgrade access roles of such users.
g. Remove / Uninstall Unused Extensions / Components / Plugins
Remove or Uninstall Components / Extensions / Plugins from the application, because attackers generally target such files for malicious script injection.
h. Server Level Administration
1. While connection to server for file transfer & related activities always use a secured encrypted connection such as (SSH or SFTP).
2. Apply secure access parameters to various configuration, setting files on server.
3. Maintain periodic database & file structure backups.
4. Use database abstraction layer to avoid SQL injection & other related threats.
5. File/Folder Permissions- Check & apply suitable file/folder access permissions. Ensure appropriate usage of Read, Write & Execute permissions applied to folder/files on server. In order to keep check on easy access to intruders.
For eg. if in case upload file functionality, then only respective upload folder should have an execute permission or else in other cases there is no need to have execute permissions.
6. SSL Certificates- Install & configure SSL certificates if required on server. SSL layer provides a certain process of authentication of sensitive information such as username & password against a plain format sent by HTTP calls.
7. HTTP security headers- HTTP security headers provided an added layer to prevent attacks and further possible security vulnerabilities.
Following HTTP Headers are being advised to be integrated-
- X-Content-Type
- Content-Security Policy
- X-XSS-Protection
- Strict-Transport-Security
- X-Frame-Options
- Public-Key-Pins
8. IP based restrictions for authentications, such as root / admin section access should be allowed or restricted to certain group of users only.
9. Block Bad Crawlers / Bots- Some automated programs are meant to unnecessary crawl through contents of site, which causes increase in bandwidth & unnecessary usage occurs. So it is advisable to block such bots at server level.
Tools to Determine and Monitor Security Threats
- Scan My Server:
a. Get a detailed security report on your website and server
b. Test for malware, SQL injection, XSS and other vulnerabilities
- Web Application Attack and Audit Framework:
a. Provides an Open Source solution to secure application
b. Find and address SQL injection, XSS and other vulnerabilities
Link: http://w3af.org/
- Web Application Vulnerability Scanner:
a. Provides facility to audit the security of an application
b. Performs black-box scanning process to determine potential loopholes in an application
c. This scanning process does not scan source code, instead it scans webpages & deployed web apps
Link: http://wapiti.sourceforge.net/
- Vega Vulnerability Scanner:
a. Open Source web security, web scanner & testing platform
b. Performs automated, manual, hybrid security testing
Link: https://subgraph.com/vega/
Conclusion
Although these measures may not be sufficient enough while dealing with real time application maintenance scenarios but definitely would help you to gain a most possible head start towards addressing security measures of your application. Also get latest insights related to Software Security at Open Source Software Security Community Portal .






